- nclv.4hp44AT8shieldDOTnet
- vincentn1colas
- 3+ years in Offensive Security
- 2+ years in professional software development
Professional Experience
|
|
|
|
|
|
Education
|
|
Master of Science in Cybersecurity, Grenoble-INP UGA |
|
|
Diplôme d'Ingénieur (MSc. in Engineering), Grenoble-INP ENSIMAG |
Technologies I used professionally, hover for details
- Created and deployed a simple pseudonymization service based on the draft Oblivious Pseudorandom Functions (OPRFs) using Prime-Order Groups.
- Design and development of a trading application which allows the creation, testing and deployment of trading strategies using Technical Analysis (TA) indicators.
- Architected a distributed scraping platform using NATS for token storage and distribution. Secured using TLS Authentication and NKeys.
- Extensively studied software security, code analysis and secure programming.
- Conducted workstation, server, firewalls and SaaS platforms configuration audits and hardening: Linux, Windows, Fortigate, Palo Alto, Zscaler, Okta, Github, Gitlab, Kubernetes, AWS, GCP, Microsoft 365 services, ...
- Implemented various attacks on embedded devices : SPA, DPA, CPA, fault attack on AES, ...
- Took part in several application audits (web, iOS, Android and thick client), red team, internal audits and phishing campaigns.
- Technical certifications and compliance audits.
- Standardisation of EDR and email gateways assessments through MITRE ATT&CK® TTPs and custom tools.
- Applied Hugging Face TensorFlow transformer models to a Natural Language Inference challenge.
- Studied different neural networks to solve the MNIST problem (VGG2, LeNet-5, ...).
- Studied the German tank problem using MLE, method of moments, eCDF and EVMU.
- Applied random processes modeling as Markov Processes for performance evaluation : quality of service, loss analysis, robustness and contention of queueing systems.
- Implemented several CAPTCHA bypass services leveraging OCR and images analysis techniques.
- Created a few web apps and APIs over the past 5 years : Go, Java, Node.js or Python for backend development / Javascript, Alpine.js and WASM for frontend development.
- Design and development of a fulltext pentesting reports search web application leveraging meilisearch (Nuxt 3).
- Developped and deployed a Word to Powerpoint pentesting reports converter entirely in a web browser using WebAssembly (Pyodide).
- Implemented various cryptographic attacks : square attack on 3 1/2 rounds of AES, generic second preimage attacks on long messages for narrow-pipe Merkle-Damgard hash functions and memoryless generic discrete logarithm computation in an interval using kangaroos.
- Experimental analysis and profiling of locality defects of an Optimal Binary Search Tree (OBST). Did the same for matrix multiplication.
- Designed and developed a JPEG encoder.
- Wrote a few component of a minimalist operating system for x86 (PC 32 bits) : IO driver, time-sharing using the PC hardware clock, virtual memory allocator, a minimal POSIX shell, a simple preemptive scheduler.
- Implemented some common concurrent programming algorithms.
- Implementation of some common algorithms for zero-sum games : Alpha Beta, Minimax, Negamax, MTD, Greedy.
- App deployment and orchestration with Docker and Docker Compose.
- GCP experience : TPUs and GPUs, IAM, Compute Engine, Cloud Run.
- Conducted cloud platforms configuration audits and hardening: AWS, GCP, Azure.
- Implemented numerical analysis methods for solving the Debye-Huckel and Poisson-Boltzmann equations.
- Extensive usage of matplotlib, seaborn, numpy, scipy and pandas. See for instance how I solved a linear optimization problem using the Hungarian algorithm.
- Wrote a lot of scripts for data processing.
- Developed several web applications with Django, Flask and FastAPI : applying TDD, implementing TOTP-base authentication, ...
- Implemented several CAPTCHA bypass services leveraging OCR and images analysis techniques.
- Developed and deployed a Word to Powerpoint pentesting reports converter entirely in the web browser using WebAssembly (Pyodide).
- Wrote a web app with Tomcat, servlets and JavaSE-14 extensively using common design patterns : Front Controller, DAO, Strategy, Factory Method, Chain of Responsability, ...
- Implementation of a Discrete Event Simulation (DES) graphical desktop application : design patterns, A* pathfinding algorithm, e2e tests.
- Designed a compiler for a subset of an advanced language. The main points were compliance with requirements, software design, validation and verification techniques, quality process.
- Performed several source code audit for clients in the banking and insurance sector.
- Studied normalization theory and relational algebra.
- Design of entity-relationship and relational schemas.
- Developed a multi-user Java database application using Oracle 10g DBMS.
- Designed a simple CRUD application using Node.js, Express, Sequelize and SQLite.
- Designed a trading application database in PostgreSQL for storing orders, trades and strategies.
- Extensive knowledge of distributed SQLite-based web application deployment.
2022-2024
Calypt/Lexfo
I was hired by Calypt, a subsidiary of LEXFO, as an offensive security consultant. Alongside this, I carry out various internal tool development assignments, several of which are now in production and used on a daily basis.
My interpersonal and technical skills have enabled me to carry out a variety of assignments independently, and then to train my colleagues in the different methodologies used: workstation audits, EDR and NDR evaluations, mapping of external exposure, ...
Working regularly with the CTI team, I take part in the search for information leaks (OSINT) for various Lexfo clients.
Finally, I share a monthly internal newsletter about in-depth technical subjects at Lexfo.
2022
Calypt internship
I joined Calypt under Valentin Baumont for my end-of-studies internship.
I have been part of web application audits, internal audits (200+ hosts), red team (1600+ domains) which led to the discovery of several critical vulnerabilities : RCE, SQLi, etc. I also conducted phishing campaigns.
I leaded various engineering tasks : a fork of BloodHound to visualize the results of nmap network scans, a fork of AADInternals to improve its data extraction capacities and I architectured an internal pentest collaborative platform.
You can find the presentation of end-of-studies internship here (in French).
2021
Adrenalyse
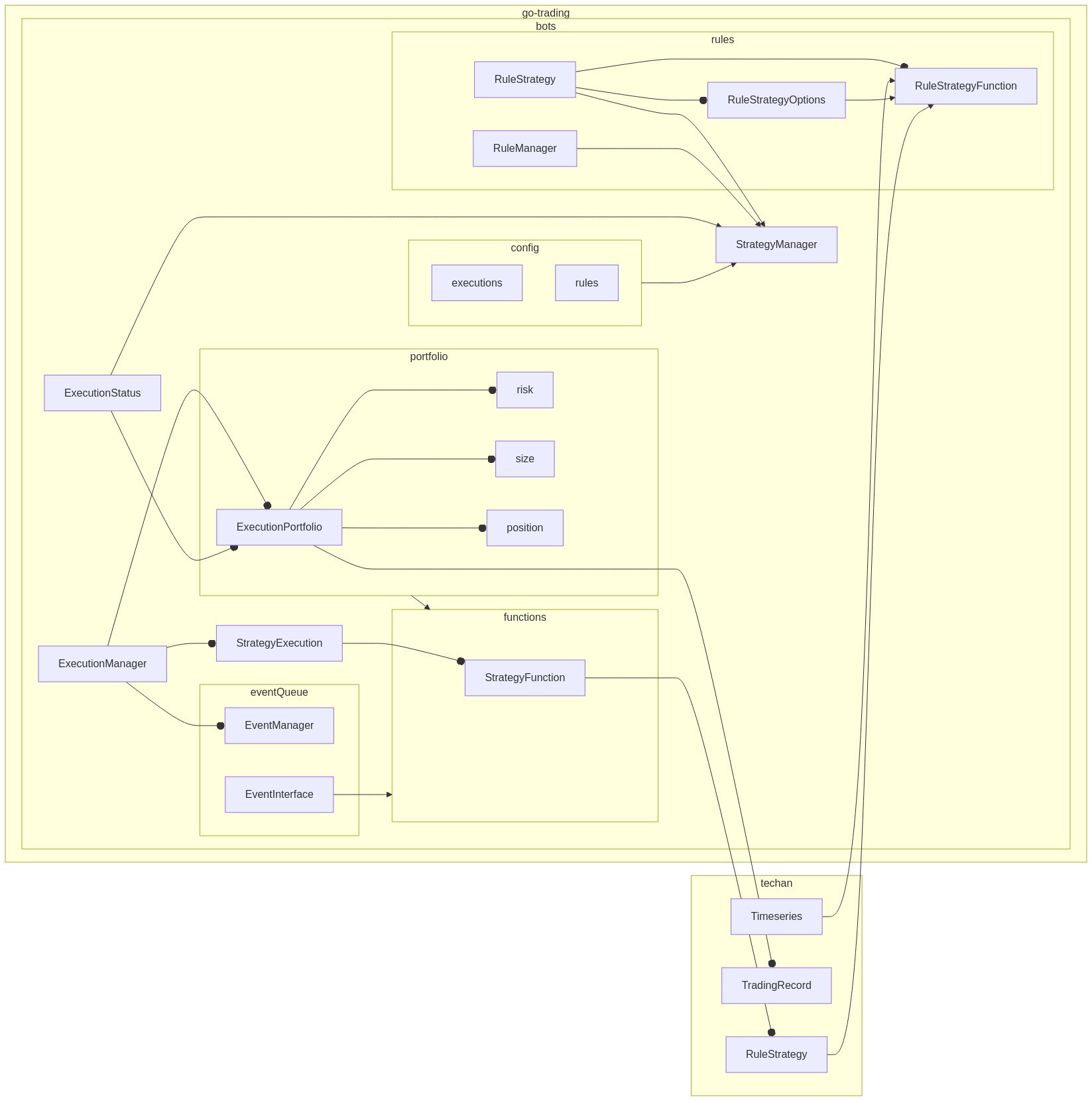
I designed and developed a trading application which allows the creation, testing and deployment of trading strategies using Technical Analysis (TA) indicators. The project architecture based on Event Sourcing makes very easy the addition of new components to implement risk management strategies. Thanks to Golang built-in concurrency constructs, you can run live strategies and simulations in parallel and control the execution and data flow of multiple live strategies.
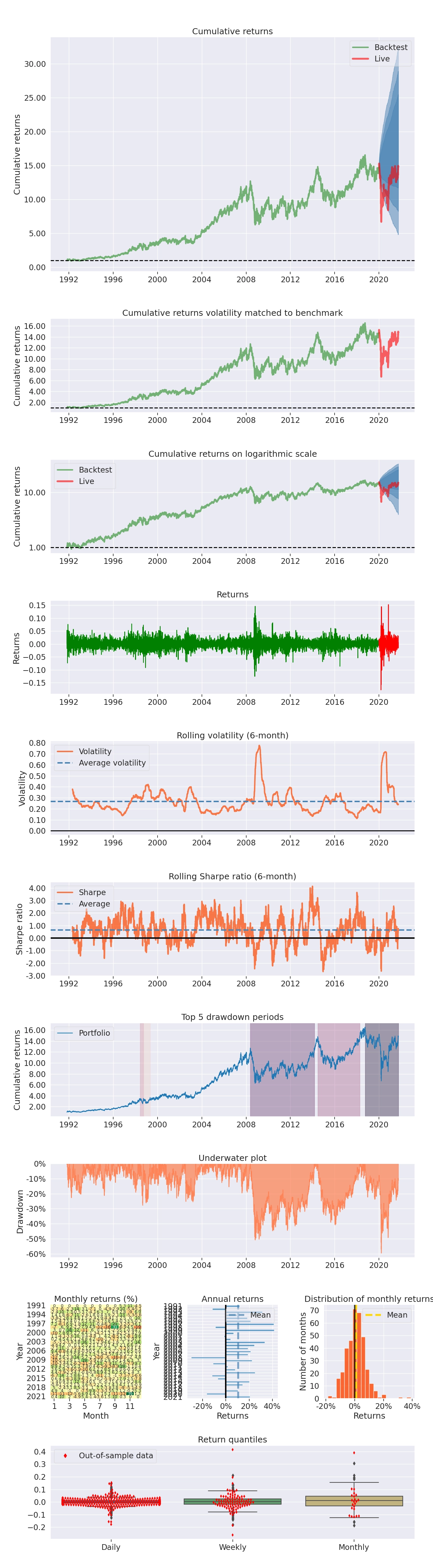
I leveraged the pyfolio library to provide insights on the strategy performance.
I have created several API clients (REST and Websockets) to retrieve market data and enabled gRPC interaction with the core application (Go server and Python client).
This project was dockerized and deployed on GCP.
More information some might find useful: